Data compliance is a crucial aspect of data protection and security for businesses. SOC 2 stands for System and Organization Controls 2. SOC 2 is a widely recognized framework for evaluating and reporting the controls and processes that organizations have in place to ensure the security, processing integrity, and confidentiality of customer data. SOC 2 was developed by AICPA - The American Institute of CPAs and is used for organizations that handle and work with consumer data.
By adhering to SOC 2 compliance, businesses can demonstrate their commitment to data security and privacy to their clients and partners. It ensures that a company's systems and processes effectively protect sensitive information, instilling trust in their customers.
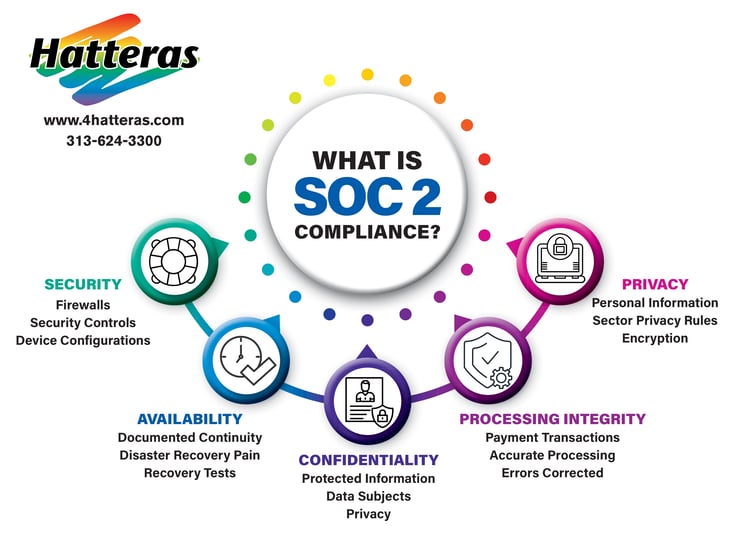
5 Key Criteria of SOC 2 Compliance
Security - SOC 2 compliance assesses the measures an organization has in place to protect against unauthorized access and data breaches. This can include measures such as firewalls, access controls, encryption, identity management systems, etc.
Availability - This measures the organization's ability to ensure that its systems and services are available and operational when needed. SOC 2 compliance can assess various factors such as performance monitoring, disaster recovery, incident response plans, etc.
Process Integrity - This criteria evaluates the accuracy of the data processing. SOC 2 compliance evaluates the controls in place to detect and prevent errors, validate data completeness and accuracy, and ensure data integrity throughout the processing lifecycle.
Confidentiality - All sensitive data is protected from unauthorized access and disclosure. This can include access controls, encryption, data storage, and data handling practices to safeguard sensitive data, both in transit and at rest.
Privacy - Privacy centers around the collection, use, retention, and disposal of personal information in compliance with applicable privacy laws and regulations. SOC 2 assesses the organization's handling of personal information and compliance with privacy laws.
How Does a SOC 2 Compliance Audit Work?
Receiving your SOC 2 compliance is not a one-time certification but an ongoing process that requires organizations to continually assess and improve their security practices. This constant assessment is essential in an environment where data breaches and cybersecurity threats continue to evolve.
Organizations undergo a SOC 2 compliance audit to demonstrate that they have implemented robust security controls and safeguards to address all of the criteria. A third-party auditor will examine an organization's processes, policies, and procedures and will issue a report based on the results of their audit. Through the audit process, an organization can uncover potential risks, vulnerabilities, and weaknesses in its controls and take the necessary steps to address them, reducing the risks of security breaches.
The Importance of SOC 2 Compliance
SOC 2 compliance is not a legal requirement. However, it demonstrates that the organization is committed to protecting customer data and industry standards. Compliance helps organizations identify and mitigate risks.
- Trust and Credibility: Demonstrates to clients and partners that a business takes data security and privacy seriously.
- Mitigating Risks: Identify vulnerabilities and implement controls to mitigate risks associated with data breaches, unauthorized access, and system failures.
- Legal and Regulatory Compliance: Meet legal and regulatory requirements pertaining to data security and privacy.
- Enhanced Customer Satisfaction: Reassure customers of the company’s ability to protect their information and that their data is handled securely.
- Business Growth Opportunities: Many companies require their vendors and partners to have SOC 2 compliance to ensure the security of shared data.
Hatteras is SOC 2 Compliant
Is your data vendor SOC 2 certified? Hatteras has proudly been SOC 2 certified for almost 10 years. We believe that trust is the foundation of any successful partnership, and we want you to have complete confidence in our data handling and security practices. When you choose Hatteras as your data vendor, you are not only gaining access to high-quality data but also the peace of mind that comes with knowing your data is in safe hands. Contact us today for your next project.




